Info Security Can Save Your Identity
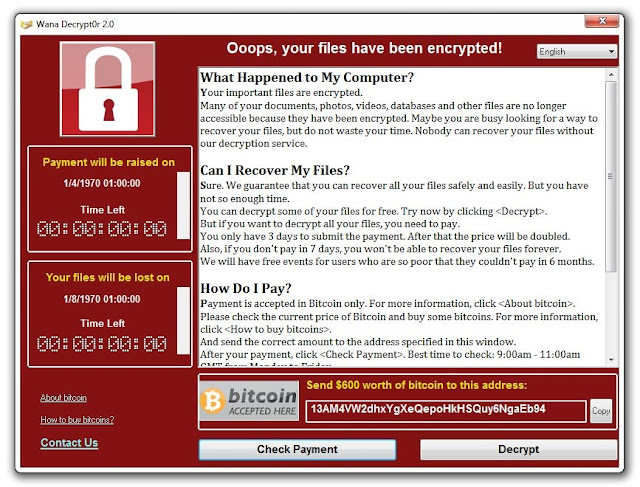
Cyber security has become a hot topic throughout businesses and organizations as new technology continues to develop. In the past several years the world has evolved around technology tremendously, making it hard for people to keep up and adapt to it. As new phones, computers, automated tellers, and security devices become familiar around the world; there are also people determined to break into them, as opposed to utilizing them correctly. These people are known as hackers, and they are dangerous. Their intention is to steal, bribe, and or threaten technology users for their information.
Safety in the household, at work, and in the economy have increasingly developed into daily task items. Whether that means enabling a home safety device, locking a computer at work, or even encrypting bank information. The number of hackers increases daily around the globe and their actions ranging from spamming your email to as far as stealing encrypted data from banks and capital markets. The US government notified 3,000 companies in the year 2015 stating they were facing attacks of economic espionage from hackers. Cyber security incidents jumped 34%, averaging $2.7 million in financial losses since 2013. The lack of proper information security only makes the hackers job easier.
Businesses and organizations have made significant security improvements and made security required more than ever before. However, organization’s security features and plans are not updated regularly, rendering the efforts near useless.
We need to understand that we are no longer in a “four wall” environment anymore; information and data are transferred around the globe and through numerous sources. Having a clear understanding of how your information is handled and how it is stolen helps organizations such as banks and retailers, as well as individuals, protect themselves from fraud. Another important factor to understand is how the threat thinks, in this case, hackers.
It would be useless to understand how these attacks occur and what motivates the attacks if we can’t prevent them properly. It’s important to prioritize and allocate the location and storage systems of resources and information that can be accessed through the internet. Having a risk assessment, making sure your business uses proper risk policies and having a clear understanding of the data flow is crucial. A very significant and important step to secure information is to make sure employees, workers or anyone that has control to your information is trained and updated on security features and policies. There are several training opportunities offered. Many companies have a data security team that manages threats and vulnerabilities, making sure the security team is familiar with common threats is something that needs to be enforced on a daily routine. With data and information being passed through multiple sources, third-parties, and any other users it is important that everyone plays their part to secure information in the workplace. In the end, your information and data are only as protected as you make it.
Sources
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf
Safety in the household, at work, and in the economy have increasingly developed into daily task items. Whether that means enabling a home safety device, locking a computer at work, or even encrypting bank information. The number of hackers increases daily around the globe and their actions ranging from spamming your email to as far as stealing encrypted data from banks and capital markets. The US government notified 3,000 companies in the year 2015 stating they were facing attacks of economic espionage from hackers. Cyber security incidents jumped 34%, averaging $2.7 million in financial losses since 2013. The lack of proper information security only makes the hackers job easier.
Businesses and organizations have made significant security improvements and made security required more than ever before. However, organization’s security features and plans are not updated regularly, rendering the efforts near useless.
We need to understand that we are no longer in a “four wall” environment anymore; information and data are transferred around the globe and through numerous sources. Having a clear understanding of how your information is handled and how it is stolen helps organizations such as banks and retailers, as well as individuals, protect themselves from fraud. Another important factor to understand is how the threat thinks, in this case, hackers.
It would be useless to understand how these attacks occur and what motivates the attacks if we can’t prevent them properly. It’s important to prioritize and allocate the location and storage systems of resources and information that can be accessed through the internet. Having a risk assessment, making sure your business uses proper risk policies and having a clear understanding of the data flow is crucial. A very significant and important step to secure information is to make sure employees, workers or anyone that has control to your information is trained and updated on security features and policies. There are several training opportunities offered. Many companies have a data security team that manages threats and vulnerabilities, making sure the security team is familiar with common threats is something that needs to be enforced on a daily routine. With data and information being passed through multiple sources, third-parties, and any other users it is important that everyone plays their part to secure information in the workplace. In the end, your information and data are only as protected as you make it.
Sources
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf
https://www.pwc.se/sv/bank-kapital/assets/cybersecurity-and-privacy-hot-topics-2015.pdf


Comments
Post a Comment